Chapter 7 Wireless Security Screen
NWA1100-N User’s Guide
72
7.3 What You Need To Know
User Authentication
Authentication is the process of verifying whether a wireless device is allowed to use the wireless
network. You can make every user log in to the wireless network before they can use it. However,
every device in the wireless network has to support IEEE 802.1x to do this.
For wireless networks, you can store the user names and passwords for each user in a RADIUS
server. This is a server used in businesses more than in homes. If you do not have a RADIUS server,
you cannot set up user names and passwords for your users.
Unauthorized wireless devices can still see the information that is sent in the wireless network,
even if they cannot use the wireless network. Furthermore, there are ways for unauthorized
wireless users to get a valid user name and password. Then, they can use that user name and
password to use the wireless network.
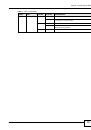
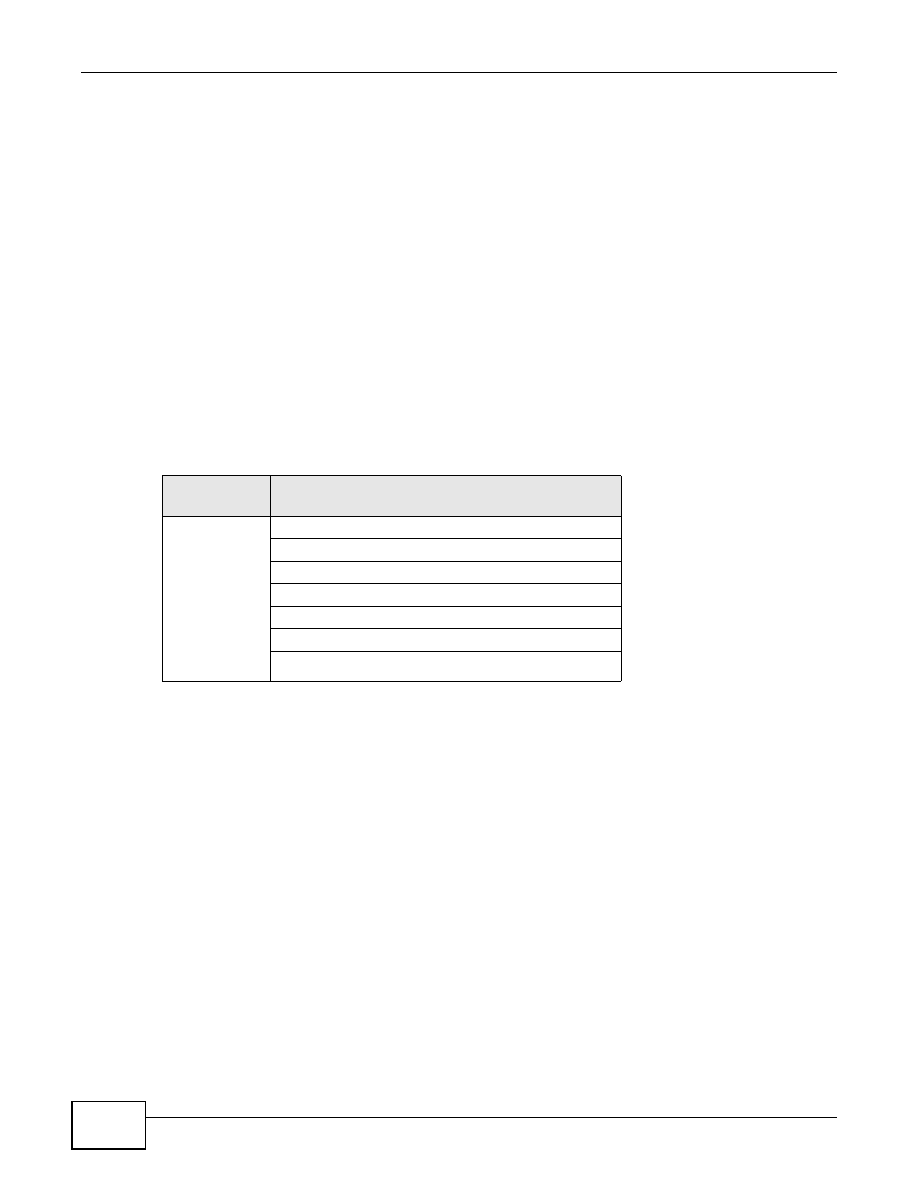
The following table shows the relative effectiveness of wireless security methods:.
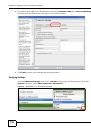
The available security modes in your NWA are as follows:
•
None.
No data encryption.
•
WEP.
Wired Equivalent Privacy (WEP) encryption scrambles the data transmitted between the
wireless stations and the access points to keep network communications private.
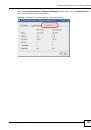
•
802.1x-Only.
This is a standard that extends the features of IEEE 802.11 to support extended
authentication. It provides additional accounting and control features. This option does not
support data encryption.
•
802.1x-Static64.
This provides 802.1x-Only authentication with a static 64bit WEP key and
an authentication server.
•
802.1x-Static128
. This provides 802.1x-Only authentication with a static 128bit WEP key
and an authentication server.
•
802.1x-Static152
. This provides 802.1x-Only authentication with a static 152bit WEP key
and an authentication server.
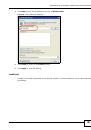
•
WPA.
Wi-Fi Protected Access (WPA) is a subset of the IEEE 802.11i standard.
•
WPA2.
WPA2 (IEEE 802.11i) is a wireless security standard that defines stronger encryption,
authentication and key management than WPA.
•
WPA2-MIX.
This commands the NWA to use either WPA2 or WPA depending on which security
mode the wireless client uses.
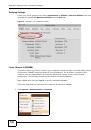
Table 12
Wireless Security Levels
SECURITY
LEVEL
SECURITY TYPE
Least
Secure
Most Secure
Unique SSID (Default)
Unique SSID with Hide SSID Enabled
MAC Address Filtering
WEP Encryption
IEEE802.1x EAP with RADIUS Server Authentication
Wi-Fi Protected Access (WPA)
WPA2